A New Wave of FakeCall Malware Targets Your Android: Are You at Risk?
2024-11-04
Author: Jessica Wong
Cybersecurity Threat Overview
Cybersecurity experts have uncovered a stealthy new variant of a notorious Android malware family known as FakeCall, which employs advanced voice phishing techniques to deceive unsuspecting users into surrendering their sensitive information. This latest iteration marks an alarming escalation in the malware’s capabilities, posing a significant threat to mobile users, especially in regions like South Korea where the malware has previously wreaked havoc.
Expert Insights
According to Zimperium researcher Fernando Ortega, "FakeCall is an extremely sophisticated vishing attack that allows attackers to nearly fully control compromised devices." The malicious software can intercept both incoming and outgoing calls, tricking victims into dialing fraudulent phone numbers that the attackers control while mimicking a normal user experience.
Malware Evolution and Infiltration
Since its debut in April 2022, FakeCall, along with its aliases such as FakeCalls and Letscall, has been closely monitored by leading cybersecurity firms, including Kaspersky and Check Point. The malware infiltrates devices through a variety of malicious app packages, including notable ones like `com.qaz123789.serviceone` and `com.securegroup.assistant`, among others.
Data Harvesting and Espionage Features
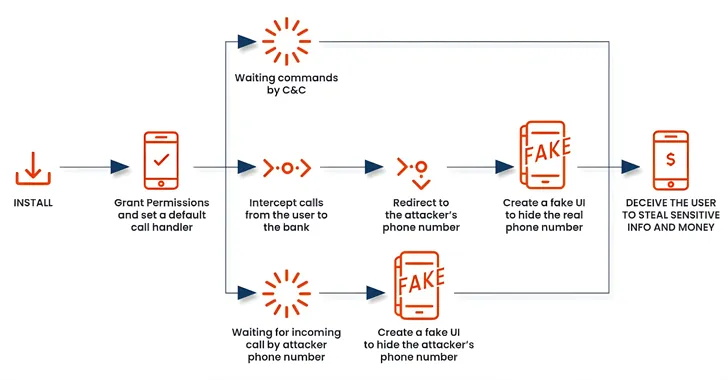
In a similar vein to other banking malware that exploits Android's accessibility services, FakeCall not only seizes control of calls but also captures sensitive information, such as SMS messages, contact lists, and even locations. Some of its more intrusive espionage features include taking photographs, recording video streams, and imitating legitimate bank call interfaces to further trick victims into revealing passwords or personal identification numbers.
Default Dialer Manipulation
What sets this new version apart is its capacity to instruct users to set the malicious app as their default dialer. This dangerous switch enables it to monitor and manipulate calls, allowing the malware to reroute legitimate banking calls to fraudulent numbers. In past attacks, users were often prompted to contact what they believed to be their bank to inquire about enticing offers, only to discover too late that they were giving away critical information to scammers.
Risk of Call Manipulation
As Ortega highlights, "When a compromised individual tries to reach their financial institution, the malware redirects the call to a number controlled by the attacker." The malware’s interface mimics a legitimate Android calling screen, displaying what appears to be the actual phone number for the bank, making it nearly impossible for the user to notice the deception.
Response from Cybersecurity
The rise of FakeCall and its sophisticated techniques reveals a significant response from cybercriminals to the evolution of mobile security measures, including the widespread use of caller ID applications that can flag suspicious numbers. In a proactive step, Google has initiated a project designed to automatically block the sideloading of potentially harmful Android apps, particularly those that request sensitive accessibility services. This initiative is being rolled out in countries such as Singapore, Thailand, Brazil, and India.
User Awareness and Precautions
The emergence of advanced malicious phishing strategies poses a serious threat to Android users. Awareness and vigilance in safeguarding personal data are more crucial than ever. Users are advised to verify the identity of callers, avoid installing apps from unidentified sources, and use up-to-date security software to help protect themselves from these increasingly sophisticated malware attacks.



 Brasil (PT)
Brasil (PT)
 Canada (EN)
Canada (EN)
 Chile (ES)
Chile (ES)
 España (ES)
España (ES)
 France (FR)
France (FR)
 Hong Kong (EN)
Hong Kong (EN)
 Italia (IT)
Italia (IT)
 日本 (JA)
日本 (JA)
 Magyarország (HU)
Magyarország (HU)
 Norge (NO)
Norge (NO)
 Polska (PL)
Polska (PL)
 Schweiz (DE)
Schweiz (DE)
 Singapore (EN)
Singapore (EN)
 Sverige (SV)
Sverige (SV)
 Suomi (FI)
Suomi (FI)
 Türkiye (TR)
Türkiye (TR)